The structure of shadow information economics

ABSTRACT
The paper represents the analysis result of a number of available scientific sources, giving a description of organization and development of the most common domains of shadow information economics, and the authors’ point of view on the subject is given.
Keywords: shadow information economics, underground economy, malware, shadow goods and services
1. INTRODUCTION
Humanity has encountered the problem of underground or shadow economics since apparition of the economics as such, but only recently, since the beginning of 20th century a profound research of the problem has begun. Ones of the most prominent scientists of the domain are Ernando De Soto and Friedrich Schneider; their researches brought significant breakthroughs to the domain. Their work is incredibly profound and defines the way modern researchers interpret underground economics today, but this scientific domain still continues its development, and what we are trying to stress in this paper is the informational part of shadow economics, which is developing fast during the recent years and can’t be simply neglected.
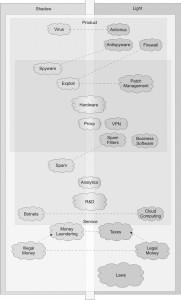
Schneider and Enste define underground economics as “Underground, hidden or shadow economy includes not only illegal activities but also unreported income from the production of legal goods and services, either from monetary or barter transactions that would generally be taxable were they reported to tax authorities.”. While this definition is generally correct, we would like to propose the following one for the shadow information sector under consideration: the individual and collective unlawful activity, related to design, production, distribution, support, and use of components of information and communication technologies that is hidden from society. In other words, shadow information economics is all the criminal information products, services and processes based on IT or using IT. The main economical elements of this domain are unlawful economical relationships, illegal business, which is related to production, distribution and use of prohibited goods and services, sphere of illegal employment. It is important to note the fact that this kind of economics merges unlawful goods and services production, prohibited by national legislations, unlawful sale and purchase of goods and services, and consume of aforementioned unlawful goods and services. Therefore, we can conclude that the main reason of shadow economics existence is a set of conditions that makes it profitable to conduct unlawful activity in the domain of information technologies. Generalized structure model of shadow information economics is represented on figure 1.
2. STRUCTURE ANALISYS
The main elements of any economy, including official and its underground counterpart are goods and services. But we consider very important to note the fact, that in information economy the line between goods and services is very indistinct. A good may become a service under certain conditions and vice versa.
Figure 1. Generalized counterpart model of shadow information economics.
2.1 Goods
Goods in economics refer to something that is intended to satisfy a need or want of a consumer and very often is tangible. In information economics tangible goods are very few and they often refer to computer hardware, whereas for the most part term goods refers to software which is generally considered to be intangible. Most common examples of goods in shadow information economics are the following:
- A large range of specialized software
- Spyware devices
- Plastic cards production and counterfeiting
- Pirated software
2.2 Services
Another side of the shadow information economy is the services provided in this domain. As well as goods, underground information services bear several distinct features. For example, they may closely interlap with the goods; the same categories may apply to the point of indistinguishability. The most common examples of services in the underground shadow economy are the following ones:
- Analytics, including search and research of vulnerabilities, market and legislation analysis, etc.
- Identity theft, such as interception and capture of identification information, credit card data, logins, passwords.
- Spam
- Phishing
- Farming
- Extortion
- Sabotage
- Terrorism
- Piracy
- Proxy servers rental
- DoS attacks
- Money laundering, using information technologies
- Botnet creation and rent
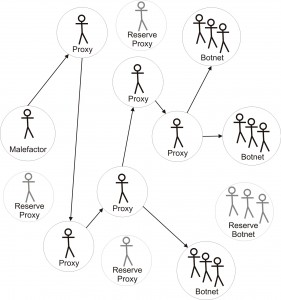
Figure 2. Generalized control scheme for a botnet.
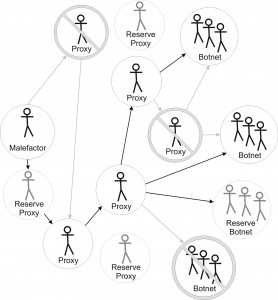
In our opinion, the struggle that takes place nowadays is mostly strategically incorrect. Even though effective against single targets, taking down one threat does not solve the more general problem, which is their appearance. For example, botnets. Every malefactor running an elaborate, working botnet that brings a solid profit usually has reserve resources, he could bring in case of emergency, or has enough experience to deploy a new one. An example configuration is represented on figure 2. Shutting down a single botnet just means that a malefactor has to lose some time to set up a new network of zombified devices or bring in his reserves, and the system doesn’t really prevent him from doing that. When a botnet is well-designed auto-recovery may be well automated taking the effort required by the malefactor to a minimum. After some of the nodes were shut, the configuration switches from the one we see on the second figure to the one represented on figure 3. As a result, taking down single botnets or proxies does not decrease their overall number. And this in turn reduces the efficiency of end-point protection. Furthermore, when a malefactor sees that some of his resources stopped functioning, he may sometimes figure out what exactly lead to their detection and try to avoid any such actions in the future.
Figure 3. Generalized control scheme for a botnet after some of the nodes are shutdown.
Figure 4. Priority research directions.
Thus, we consider that the main strategic direction of work in this domain should be the study of interactions between the participants of shadow information economics. We consider that the most notable of them should be the following:
- Distribution of goods and services in the domain of shadow information economics
- The principles behind demand and supply shaping
- Business model
- Price policy model
- Competition principles
- New market players
- Elimination of participants who failed in the struggle.
3. CONCLUSION
The main conclusion that could be drawn from this paper is that a complex strategy proposing a solution to the problem of underground information economics is desperately needed. Current measures taken are even though effective to a certain degree, but are not enough. We see the following three principles as the pillars of a possible strategy:
- Legislative base improvement. This includes economic regulation base that will significantly decrease profitability of underground activity.
- State-level partnership in counteracting this problem.
- Creation of new workplaces, tax system reformation, and developing a much more efficient struggle versus corruption.
REFERENCES
1. Ohrimenco Serghei, Hârbu Eduard, Bortă Grigori, Sclifos Constantin, Solonenco Oleg, Levandovsky Vlad, Storoj Oxana, Pavlova Lilia. Information security in SMB. Laboratory of Information Security. [Online] [Cited: September 10, 2012.] http://security.ase.md/materials/publications/index.html?artNr=9.
2. Охрименко, Сергей and Саркисян, Агоп. Подпольная информационная индустрия. Laboratory of Information Security. [Online] [Cited: September 10, 2012.] http://security.ase.md/materials/publications/index.html?artNr=3.
3. —. Экосистема Информационной Безопасности. Laboratory of Information Security. [Online] [Cited: September 10, 2012.] http://security.ase.md/publ/ru/pubru121/TOM_2-rebuilded_Pages_31_-_36.pdf.
4. —. Сенчестият Пазар на Инфомационни Технологии. Laboratory of Information Security. [Online] [Cited: September 10, 2012.] http://security.ase.md/publ/ru/pubru120/scan-articles-Ravda-Bulgaria2009-v-85prc_%28site%29.pdf.
5. Бортэ, Григорий. Теневая Информационная Экономика. Laboratory of Information Security. [Online] [Cited: September 10, 2012.] http://www.security.ase.md/materials/si2011/Security_inform_2011_Pages_94_-_96.pdf.
6. —. Исследование жизненного цикла вредоносного программного обеспечения. laboratoryofInformationSecurity. [Online] [Cited: September 10, 2012.] http://security.ase.md/materials/publications/index.html?artNr=6.
7. Chiesa, Raoul. Cybercrime: reasons, evolution of the players and an analysis of their modus operandi. Bright. [Online] July 1, 2010. http://flarenetwork.org/report/enquiries/article/cybercrime_reasons_evolution_of_the_players_and_an_analysis_of_their_modus_operandi.htm.
8. —. Cybercrime & underground economy: operating and business model. Flare Network. [Online] July 1, 2010. [Cited: July 22, 2012.] http://www.flarenetwork.org/report/enquiries/article/cybercrime_and_underground_economy_operating_and_business_model.htm.
9. Vulnerability Markets. What is the economic value of a zero-day exploit? Boehme, Rainer. Dresden : Technische Universitat Dresden, Institute for System Architecture.
10. Greenberg, Andy. Shopping For Zero-Days: A Price List For Hackers’ Secret Software Exploits. Forbes. [Online] March 23, 2012. [Cited: July 20, 2012.] http://www.forbes.com/sites/andygreenberg/2012/03/23/shopping-for-zero-days-an-price-list-for-hackers-secret-software-exploits/.
11. —. Meet The Hackers Who Sell Spies The Tools To Crack Your PC (And Get Paid Six-Figure Fees). Forbes. [Online] March 21, 2012. [Cited: June 21, 2012.] http://www.forbes.com/sites/andygreenberg/2012/03/21/meet-the-hackers-who-sell-spies-the-tools-to-crack-your-pc-and-get-paid-six-figure-fees/.

Comments close